| Name | Sample Link | Personal Rating * | MD5 Hash |
|---|---|---|---|
| WannaCry | Github PMAT Husky | 6.5 | db349b97c37d22f5ea1d1841e3c89eb4 |
This rating is take from the moment I did this analysis. In the time being, this can change because my skills have progressed. Only take it as a point of view of this moment.
Static
Hashes
First, we get the file hashes:
| MD5 | SHA256 |
|---|---|
| db349b97c37d22f5ea1d1841e3c89eb4 | 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c |
A short search on VirusTotal give us that this is a malware by 68/71 security vendors.
Strings
Using floss we get some curious strings. Some of them are functions, but also files:
1
2
3
4
5
6
7
8
9
10
mssecsvc.exe
KERNEL32.dll
MSVCRT.dll
launcher.dll
tasksche.exe
USER32.dll
ADVAPI32.dll
SHELL32.dll
OLEAUT32.dll
WS2_32.dll
This string appear sometimes:
1
2
3
4
5
__TREEID__PLACEHOLDER__
__USERID__PLACEHOLDER__@
r7J5aeRrLmBr/hb9bYEXZm021DpdeTNoOYYvv0T+lNQjdiR7LkNN0FqZ2Qzqw65gTEL0H7NFit4KrHRg2HN4SahBmrhvWBjV/yKYK0wmglNwlk3r0PAct+NWmZF9JagZE2BiHbiBBlEI29F/UN75bXD9l1Q/0Kcz/Uzh/MvveVF258rAjFInwG8ZqxCM0MpoC5PWOaW1RmLjnuhMd74K8xACxh2hsIyPd7kVjMwf8UmA5w0+lN9bWPytL5XZQURL/A2sPZc6I7FterYn/pBL8H1O61MDngY0GkuVTzuVx7mTX+Ccrds2xTkQwaogLGN+0+i3/YIs8EYnxOt7l1NDuZABViyeCEGb/luBxbAnQSnGpRwJvrmoY8toD09ukeWgjCJ2Ai8ExtpIChU2sNx85eQThEAoN0zmSyg9o30K4Tsov1ZTIp/X95Se8KnwQi9dR3QYKc8yBBSm8kVJ6GGpKQNWQ6P8c+jFICxRXCr61hUCrp7l3wPkNw013Rl5fmPpPiQo6CeAMsuJNiwYxfPyi07CMqjnVLoeG6OOTWljvz8y+FTfVZCZBsFBDF9466IHD5vRZFXNyMK9f8lBAf/FKP5U2etKvFr+y0UzeQ50K1VhCDWxQIyPi78hG4ytDPs/1abcyyE+Zz82FmWbwA6SnUjO/25jXVospykFgiPFrDMiCFBF0uut8WqNe7+7HmU8v+Ig4F+1eQ9MSR7WXiFiZXWHXj1crLYpGpFd95oYovDOvw+yWgkxqIT+R6V2F+o5RYMdg9YCMTgtiyu70wCgucw9RU1kqGkiYCOkKL0aWDOzuBO5S5CkTYAJdzE+W5XDCgX6cpWGhJ0FasNnH3NAfjYI0LszwpEDu98OBY+zmtTlZtC3oPFMWAC/Z0AlaKppAPj9wC+wTUvHaYebKOjTujZqL+ysbIsiANOz9as1cnBUVVGzas9ZZKOX83TZfRF3UTrZM1UxnxEDg+3tUKdUvZGixYunoOnldp/9oFIHacUCtHo6CGE6jgS0iRgbi3YfFyvD/+d8KjQ+vZREmGxZ+/yKtIKXOsz9+pMo0OiDcvtF3PlEUS6xy7ekKLyUOWAWFoR9s+H2bIXCRIo/Jdns9MdGkdz8+tco7bthLrJghq4A46rewPPAV1vte6FLbSLJonwdvJda4x4RldJLN4mRCT4nZ3t7O8oI/ePQxRdVXrtGJ0OQ5HlQrbdkvR6R7+hr8VdXdUcfdnHbb1BfzJiGI/e6+DyAxsdl29vVlXV0cVx6dNEAIkOVnLPajGppXEoiUc7sGlzOdU52RJCjgIVLG5Q/eKkNO9LTendYxljGopQHZ2SJXus2AQl97m0T6kswRtRBzqKS1cRYKce1MXGWmjsiMIrLz8NerBzf2NnrmQSBxUTIuUPqxoxBajr
XUEZWScY9Wd5NxIaAymV7D4nhYxXPgJPYplP/JZLRdRNsF07V9WLht3JteSO2y+ZBce5J9eVRWen7Fyf2PSE0P8C+x5s2jXYRgElfKZEpNmQqKR+3mq80O0/iY1BfcnkOVT4EryG31z26cgh6xnUN9uStuyFWstej8ORiGNY+gy+h9Ma1tbKzaCvubVAwWAbfqzlWJKaHyKsSZT207h0dRNDbrp4uTBoP/LB966BONJNWl+6qmiVJBl7gIEY24zNVSFsVzZCRwz/J3X4PhBfo4fFiQqEDAlwqNdfKuQT+86wYbKCfh6d+eoowVCM20fpL1Ql20GyOlLnxzKto9h8OG0TfHF3ReH8o4ilB6QLiqSCauuitMHUWX0dznaakzpj3WtoX2nZBmh7lvVTTg9RfXNAXOo3/Q0TEUP9xACBl3h1Q+YCtqN2s4O6/Z//XnFQ4VaLhUS2u6nxobFloPVAjbXp7POdoj3lBrxUYoaYqr9btwiNrigI7OKz7d1f0FDY4e4vzjWEJyqzjdBzqrFqw7+FotuAypht8B0Dkm06jgy2dhSd1W+R0TADSowcrOJOuPYm7VtniJEy+Bz/F2czbt881JIA1YhSOijvyUoG9Rt2f+P7/3AhIdBcMW8Bf6m+89BsOMx/VN6XFq93fAQTQGTbhpnoEI2vD0wF1cCkcwsGsgUGkyyxbj3Gq0+5VcXhEYujDvs2WkiFegKTK8w/IUThynLN1O+08NZ5jqKMPw9GYeSGCpGeEv8jENZhKqfV9POm9IVUMCjJNvGXgKbsTMFo3qU8fiiaMzd6zFXT4ow3bcoyeYfkXuiNZQH3ulbB5eVwCWiBuWlGdGKDnCsxGOmymI6ha9OUL/Iyqw8JIjaILGTlhCvTI+ZX+z7XKdNz4ATCsddiVKkwIyiRllfMN9ZaAZCB8WNOIyNi9G2/OxjyvqmKtwsiOB3j7ceyAJa/QSEeA8zHsIXiCC36PFVDcdmCqD81xmIOWCZTMcaWb+6j8DGOazwSuD44d/tU0usP79h4/byLy3pVNEHlFEEeIi45DgUa1X07NxmSzDrouta37//FTiA40EiAhsuPdWdj/kDql9VPHC6uK8TaiztM9uP97Ytl3LNLcBCnaUxfzUVgpVDASsdYKr0B6i9cstHZxOqWRnZAIjK0MCo4ccL/7hDAOG2NamNlJGk5fO93DTklHdQLoyLJvzSQgIU8Cvk2pRXpw01iwIbi+5VbFNK1SmFhmxNZJI1dk4syjNrRFArd9m04gaeKZ1RC7AAe5ZNSXGWZhwXXoVyehwhEg0wpV7hAg0GDe+JseaB3CCvN2dtQhNgkCUbtDJo7+DBsDJMFw+zTxuyORRMQ79F2wxDRoXagsvq26XV/agpNU21MWzi6yRWXiOIu4ibLqhDsAaw3uSUTqwwwvQ0jtYqQpy2QBSgYE0QrNHOME8g9m+nkNMVAdDDDiCKZ/+3CmrNSY93T90CYblH3/arSy3/Ikpfppab7v/ttDltmWAYtUFrPXSAzzfZIbOuF76kg2Cxr6OmdaANIZv73EGYutwccQhLchwtdwE6wocqyfxD7d6UnbC+IJn84Hrp/IZl8/GMYHMaYujmbfmpDkuMrJVG9GFDyYtmMEoBed0AiRihI/19JQIvCeEER6Z0LS4orDQQB5LQcRHKUDXyiU8whdEYNVyve1MAWt/TjSAZNVoLog3MEfx2qlXZFKZkmmBch01PeIpzevpf9xdsPItHzzgBLiyk2PVZG5eOOjiyo6DysGdE8JHCwqJidXARxJG1+9nybvRj55sH2KMmgId7x7/L1HK6oVRC/h1frsvol3nVUaDdRa7jwmslNIRERnJbWQLwHQvbbgcZJl0aqNH6mWJ5QRK1t54d/Tu44oZ62xqmCgzVvDxe9ws1lxtW2urNSAlKN5pLn+nnG+xPt3grXpVnGk78g0IMobHc1dF+AtRYDOMoCfw+i8ANdrfp8W+UkvMNkHNySjWOI7NnaGBs/ZJb/2RDuN+hIY6wCtZNTRLqn5g0IS3bHdIZZeBI2TuZsmNidiw0xbgBbBR7bJMpFFk5HN41YufB1uCsXly67Ex1FaMMHB0FoejOWsTPK/jVDwBliwqguSDzJRWK/1uoz55aWCR7ux0Yjxp3fEHgITZMj1q4yHiPfFL3c31lwoqp8CSSGMfqtFVuhCH8V2F/fV5J6KE6ArnLZs+GdscOUXQAg46tyOhgQYXwpvMrFOJfYphOxGSIpjw4ovTaz1IHdJYJp9CPAfS1jZwyOEg2QSREx99N8IUkJcSXnVVzDUUuJpws2fnPBt6rk7MwoGUs2j3nRxxm77wlZHTInHxJz2QqbsQGqKOMTmEOtwrUg+ZRAJJbBTJ9I+mFbDsZulqVDGrK80QV+dcARKE7F0PTFvZwAAttjgd3vOOhsBFvePugEd4Aame1goNc70x6Lb9FSGjRhO/NXxTLldTc3bh47SlfKRjiOcxRZOlOXrEdNUUSNwRWbsK3woSTj3FsP0eOy/Bs94RtL338bTcpVUBsu/SApl38h2FmRUZLNADvcmsNpd20MGUcBtoXz1qMpyrzGRY60wdFsCsvwiP5shGkqmJKh2tLo1g/2utoHAzhEPwh05oAxG4M1jYKxa7lUXqpdTAOgrsLgHFcp9hxN9PdrHAQaAr3kLbABSoknoza6/P7JURK3jZWBn+Ut8
SMB3
We have a reference to a computer:
1
2
3
4
5
6
7
SMBr
PC NETWORK PROGRAM 1.0
LANMAN1.0
Windows for Workgroups 3.1a
LM1.2X002
LANMAN2.1
NT LM 0.12
A website appear:
1
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
Some CopyRight mark:
1
inflate 1.1.3 Copyright 1995-1998 Mark Adler
The ransomware name appears as well as some file, and file handling instructions:
1
2
3
4
5
6
7
8
9
c.wnry
WANACRY!
CloseHandle
DeleteFileW
MoveFileExW
MoveFileW
ReadFile
WriteFile
CreateFileW
It is using some kind of encryption:
1
2
3
4
5
6
7
8
9
10
11
Microsoft Enhanced RSA and AES Cryptographic Provider
CryptGenKey
CryptDecrypt
CryptEncrypt
CryptDestroyKey
CryptImportKey
CryptAcquireContextA
cmd.exe /c "%s"
115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
And changing permissions:
1
icacls . /grant Everyone:F /T /C /Q
We found some files with different languages:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
b.wnry
c.wnry
msg/m_bulgarian.wnry
msg/m_chinese (simplified).wnry
msg/m_chinese (traditional).wnry
msg/m_croatian.wnry
msg/m_czech.wnry
msg/m_danish.wnry
msg/m_dutch.wnry
msg/m_english.wnry
msg/m_filipino.wnry
msg/m_finnish.wnry
msg/m_french.wnry
msg/m_german.wnry
msg/m_greek.wnry
msg/m_indonesian.wnry
msg/m_italian.wnry
msg/m_japanese.wnry
msg/m_korean.wnry
msg/m_latvian.wnry
msg/m_norwegian.wnry
msg/m_polish.wnry
msg/m_portuguese.wnry
msg/m_romanian.wnry
msg/m_russian.wnry
msg/m_slovak.wnry
msg/m_spanish.wnry
msg/m_swedish.wnry
msg/m_turkish.wnry
msg/m_vietnamese.wnry
r.wnry
s.wnry
t.wnry
u.wnry
There is a clear text XML:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges>
<requestedExecutionLevel level="asInvoker" />
</requestedPrivileges>
</security>
</trustInfo>
<dependency>
<dependentAssembly>
<assemblyIdentity
type="win32"
name="Microsoft.Windows.Common-Controls"
version="6.0.0.0"
processorArchitecture="*"
publicKeyToken="6595b64144ccf1df"
language="*"
/>
</dependentAssembly>
</dependency>
<compatibility xmlns="urn:schemas-microsoft-com:compatibility.v1">
<application>
<!-- Windows 10 -->
<supportedOS Id="{8e0f7a12-bfb3-4fe8-b9a5-48fd50a15a9a}"/>
<!-- Windows 8.1 -->
<supportedOS Id="{1f676c76-80e1-4239-95bb-83d0f6d0da78}"/>
<!-- Windows Vista -->
<supportedOS Id="{e2011457-1546-43c5-a5fe-008deee3d3f0}"/>
<!-- Windows 7 -->
<supportedOS Id="{35138b9a-5d96-4fbd-8e2d-a2440225f93a}"/>
<!-- Windows 8 -->
<supportedOS Id="{4a2f28e3-53b9-4441-ba9c-d69d4a4a6e38}"/>
</application>
</compatibility>
</assembly>
We have a list of files extension, probably the files that this malware handle.
PEview
In PEview we can see that the malware is not apparently packed. We can see the time this malware was compiled, probably this was modified:
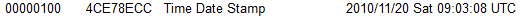
We can check the difference between the Virtual and Raw Data sizes:

There is a difference of 1.078 between both of them, so it may be a packed malware.
In the Address Table we can see some weird imports, like URL handling:

Or some unknown:

Cutter
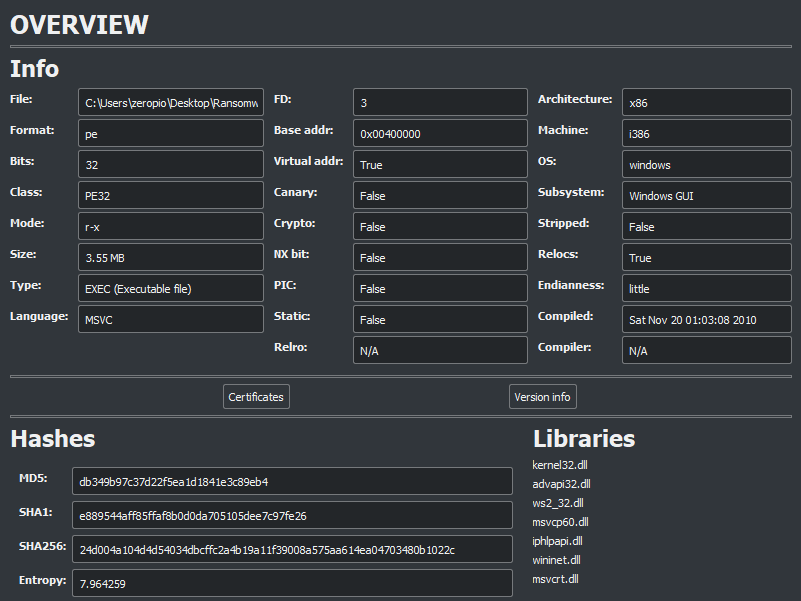
Here we can confirm the file hashes and get the architecture, 32 bits:
Here we can get the assembly code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
0x0040813f nop
139: int main (int argc, char **argv, char **envp);
; var int32_t var_14h @ esp+0x28
; var int32_t var_8h @ esp+0x3c
; var int32_t var_41h @ esp+0x75
; var int32_t var_45h @ esp+0x79
; var int32_t var_49h @ esp+0x7d
; var int32_t var_4dh @ esp+0x81
; var int32_t var_51h @ esp+0x85
; var int32_t var_55h @ esp+0x89
; var int32_t var_6bh @ esp+0x8b
0x00408140 sub esp, 0x50
0x00408143 push esi
0x00408144 push edi
0x00408145 mov ecx, 0xe ; 14
0x0040814a mov esi, str.http:__www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com ; 0x4313d0
0x0040814f lea edi, [var_8h]
0x00408153 xor eax, eax
0x00408155 rep movsd dword es:[edi], dword ptr [esi]
0x00408157 movsb byte es:[edi], byte ptr [esi]
0x00408158 mov dword [var_41h], eax
0x0040815c mov dword [var_45h], eax
0x00408160 mov dword [var_49h], eax
0x00408164 mov dword [var_4dh], eax
0x00408168 mov dword [var_51h], eax
0x0040816c mov word [var_55h], ax
0x00408171 push eax
0x00408172 push eax
0x00408173 push eax
0x00408174 push 1 ; 1
0x00408176 push eax
0x00408177 mov byte [var_6bh], al
0x0040817b call dword [InternetOpenA] ; 0x40a134
0x00408181 push 0
0x00408183 push 0x84000000
0x00408188 push 0
0x0040818a lea ecx, [var_14h]
0x0040818e mov esi, eax
0x00408190 push 0
0x00408192 push ecx
0x00408193 push esi
0x00408194 call dword [InternetOpenUrlA] ; 0x40a138
0x0040819a mov edi, eax
0x0040819c push esi
0x0040819d mov esi, dword [InternetCloseHandle] ; 0x40a13c
0x004081a3 test edi, edi
0x004081a5 jne 0x4081bc
0x004081a7 call esi
0x004081a9 push 0
0x004081ab call esi
0x004081ad call fcn.00408090
0x004081b2 pop edi
0x004081b3 xor eax, eax
0x004081b5 pop esi
0x004081b6 add esp, 0x50
0x004081b9 ret 0x10
0x004081bc call esi
0x004081be push edi
0x004081bf call esi
0x004081c1 pop edi
0x004081c2 xor eax, eax
0x004081c4 pop esi
0x004081c5 add esp, 0x50
0x004081c8 ret 0x10
We can even see here the URL we found with floss and the functions from the Address Table of URL handling. The decompiler guess this code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
/* jsdec pseudo code output */
/* C:\Users\zeropio\Desktop\Ransomware.wannacry.exe.malz @ 0x40816c */
#include <stdint.h>
int32_t main (void) {
int32_t var_14h;
int32_t var_8h;
int32_t var_41h;
int32_t var_45h;
int32_t var_49h;
int32_t var_4dh;
int32_t var_51h;
int32_t var_55h;
int32_t var_6bh;
ecx = 0xe;
esi = "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com";
edi = &var_8h;
eax = 0;
do {
*(es:edi) = *(esi);
ecx--;
esi += 4;
es:edi += 4;
} while (ecx != 0);
*(es:edi) = *(esi);
esi++;
es:edi++;
eax = InternetOpenA (eax, 1, eax, eax, eax, eax, eax, eax, ax, al);
ecx = &var_14h;
esi = eax;
eax = uint32_t (*InternetOpenUrlA)(void, void, void, void, void, void) (esi, ecx, 0, 0, 0x84000000, 0);
edi = eax;
esi = *(InternetCloseHandle);
if (edi == 0) {
void (*esi)() ();
void (*esi)(void) (0);
eax = fcn_00408090 ();
eax = 0;
return eax;
}
void (*esi)() ();
eax = void (*esi)(void) (edi);
eax = 0;
return eax;
}
It is opening an URL. If the URL doesn’t work the program close it.
Dynamic
We will start by detonating the malware with administrator privileges. From this view:

The first detonation, with inetsim enabled will not do anything. But with that turned off, we will have this:
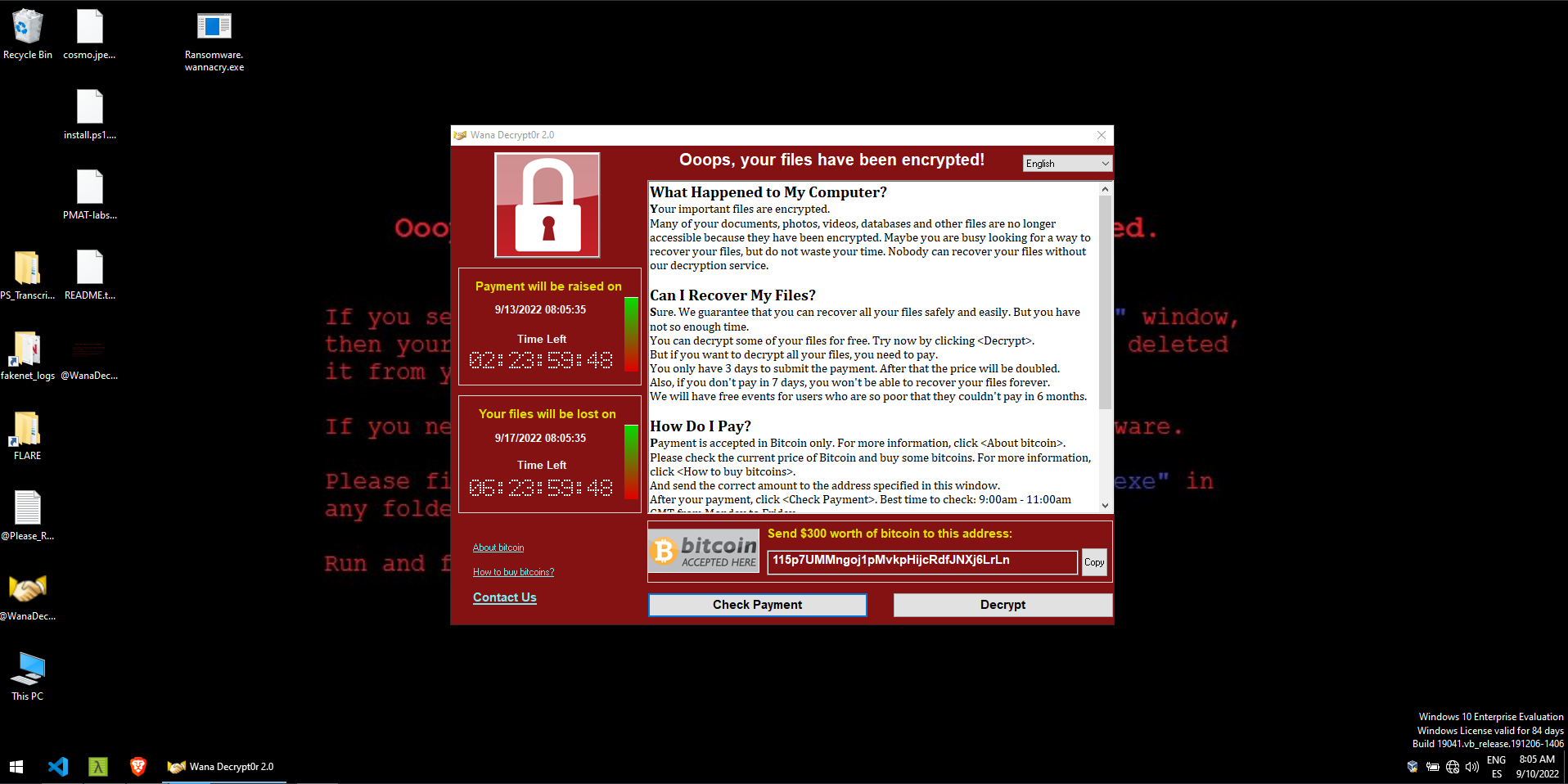
Network Indicators
Even though we don’t have internet connection to make this malware works, we can start wireshark with this malware executing. Once we launched it this lines appear:
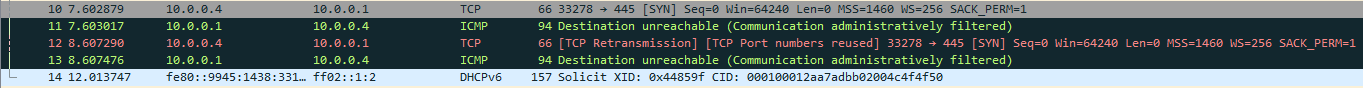
Soon, our computer start searching other computers on the network:

In the other hand, TCPview show this once the program has started:
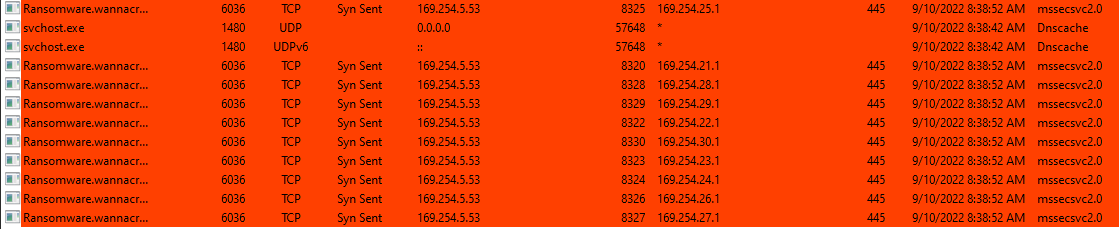
We can see it trying connection with some IPs in the port 445 (SMB). If we wait a while, we can see a .exe program has appear:

Host Indicators
As we don’t need internet (or at least inetsim) to run this malware, we will try to find the host indicators. We have seen a bunch of different files during the basic phase, let’s try finding them now.
We will use procmon filtering by the malware file name. This will print a bunch of information once it is launched. We can found the name of one of the files in the floss . This file was created under C:\Windows at the moment of the detonation.
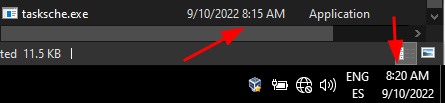
We can see in procmon that this binary has been from wannacry:

We filter now by the PID (in this case 5796) and the Operation CreateFile. We will see a new process started. We can see the creation of weird files:
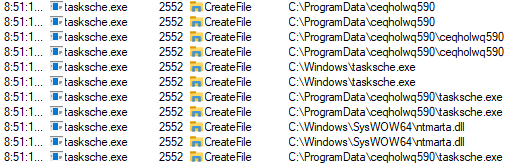
There we have many files we have found as strings in the binary:
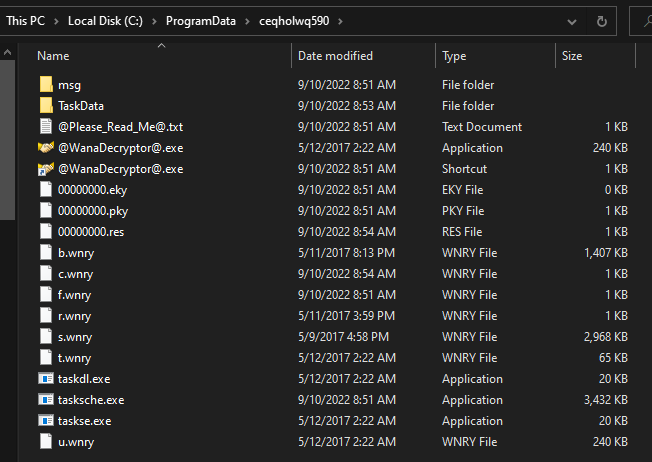
Also, a process for persistence is created with the same folder name:
Review
We can assure that this binary is a malware, specifically a ransomware. Wannacry encrypt all the user files, add persistence to the target and search in the network for other computers with SMB, to infect them.
This malware doesn’t work with internet connection.